What I wish i knew about container security
Watch talk on YouTubeBAseline
- Linux is like a hammer and containers look a lot like nails
- Containers aren’t real: They are just processes with besser isolation
- IPTables is complicates
Hard parts
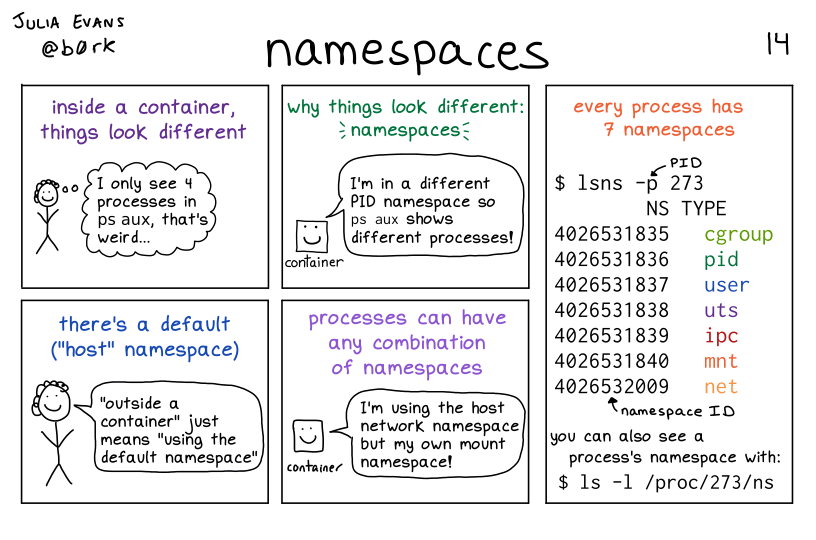
- The kernel is shared we only predent to seperate processes through namespaces
- Filesystems: Containers bring a bunch of filesystems and sharing filesystems between multiple containers
- Softlinks are hard to do right because they point to a path and not the data itself
How did we get here?
- Unix with a buch of tools we still use
- Linux (originally designed to for the desktop)
- Kernel gets iptables
- The rist concept of namespaces
- More hypervisor stuff and official user namespaces
- Containers (first lxc then docker)
Sandboxing
- In browsers: They must protect the user from malicious content
- In containers: PRetty much the same - both run untrusted code that has to be isolated
Namespaces
- Better isolation from other processes including resource constraints
- But: The shared kernel interacts with all processes (so kernel bugs can affect all namespaces)
Improvements
- Secure Computing: Implement a secure state that we transition into before the process actually does stuff
- Paravirtualization: Instead of system calls to a shared kernel we make hyper-calls to the hypervisor
- Virtualization: The classic virtualization where everyone hosts their own kernel
Stuff to look out for
More or less a bit of advertisement
- Edera: Container native hypervisor without a shared kernel
- Styrolite: Rust-based container runtime sandbox
- eBPF and Tetragon for prevention and monitoring